How
The U.S.
Hacked
ISIS
In the fall of 2016, a military unit called Joint Task Force ARES launched a classified military mission called Operation Glowing Symphony to knock ISIS’s media operation off the Internet.

Step 1: The Plan
ARES operators discover ISIS is using just 10 core accounts and servers to manage the distribution of nearly all of its content around the world. If ARES could gain access and control those, it would hobble the group’s media operation.
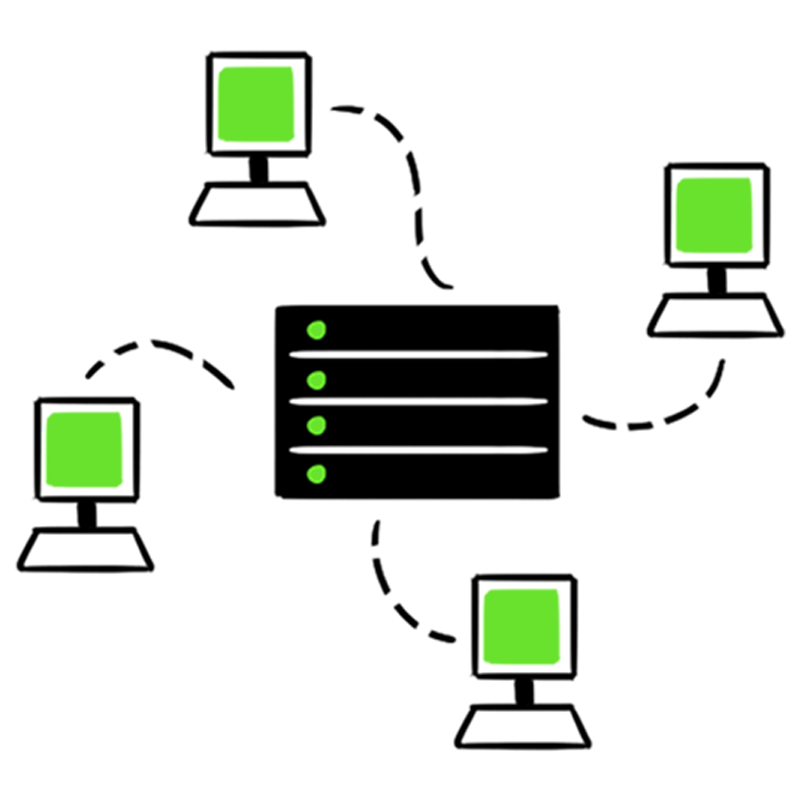
Step 2:Cracking The Network
Through several methods, ARES operators get into ISIS’s network. They create tantalizing emails — phishing emails — plant malware, open back doors and leave spyware.
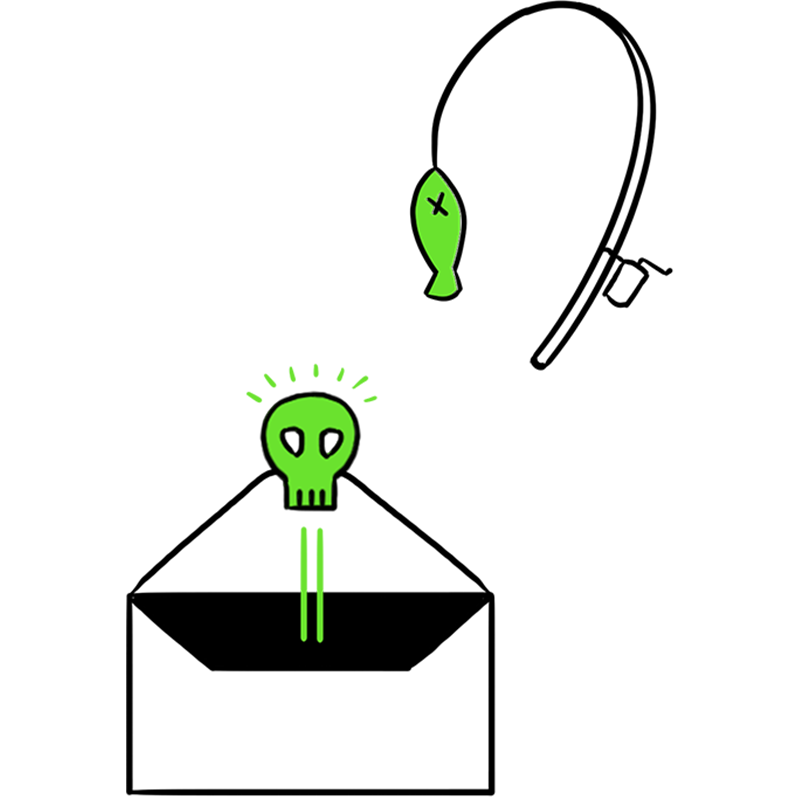
Step 3: Reconnaissance
ARES operators give themselves credentials and administrator privileges and begin to look around — at emails and their content, at the relationship between ISIS fighters — to inform their target lists.

Operators spend months practicing to surgically target ISIS content on overseas servers.

Step 4: The Attack
November 2016: ARES operators log in to ISIS accounts, delete content, crash ISIS servers, misconfigure network settings and change passwords.
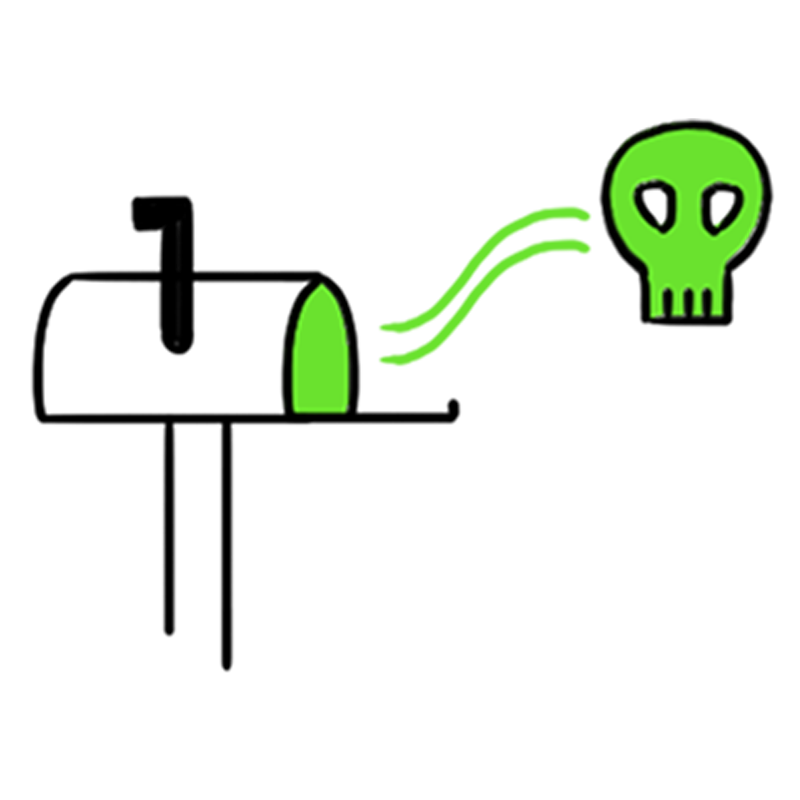
After the hack, ISIS members find themselves locked out of their accounts, frozen in cyberspace.

Step 5: Continued Operations
Operation Glowing Symphony continues today with a new variety of attacks.
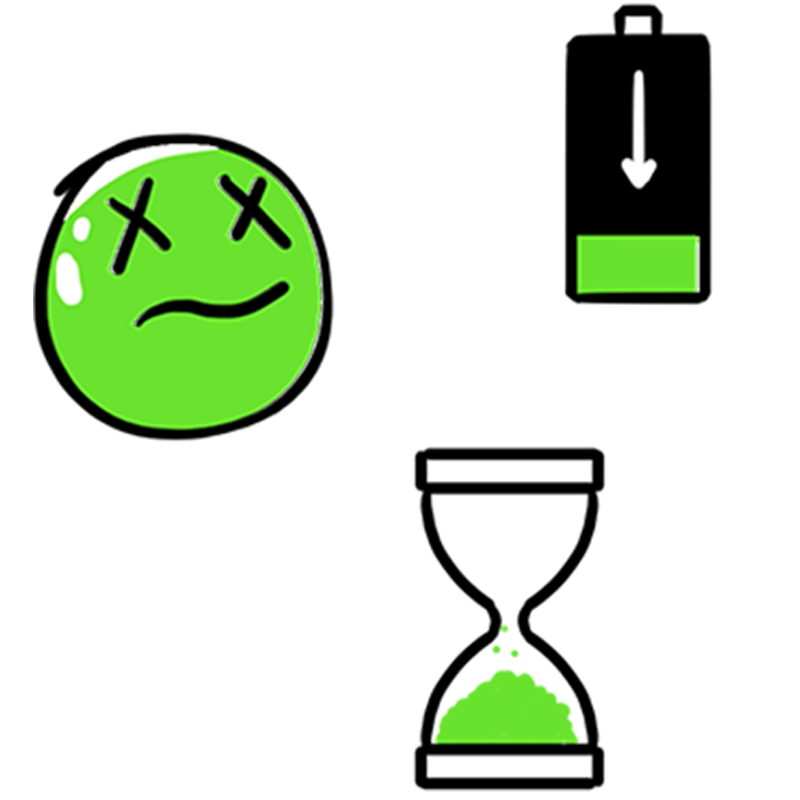
ARES is remotely draining cellphone batteries, slowing down the ISIS network and looking for ways to erode ISIS morale and sow discord among fighters.

The End